
Encryption is basically vital as a result of it secures knowledge and data from unauthorized entry and thus maintains confidentiality. Right here’s an article that will help you perceive “w_hat is cryptography “_ and the way can or not it’s used to guard company secrets and techniques, safe categorised info, and private info to protect towards issues like identification theft.
Right here’s what I’ve lined on this article:
- Introduction to Cryptography?
- Encryption Algorithms
- How numerous Cryptographic Algorithms Works?
Now, I’m going to take assist of an instance or a situation to clarify what’s cryptography?
Let’s say there’s an individual named Andy. Now suppose Andy sends a message to his pal Sam who’s on the opposite aspect of the world. Now clearly he needs this message to be personal and no person else ought to have entry to the message. He makes use of a public discussion board, for instance, WhatsApp for sending this message. The principle purpose is to safe this communication.
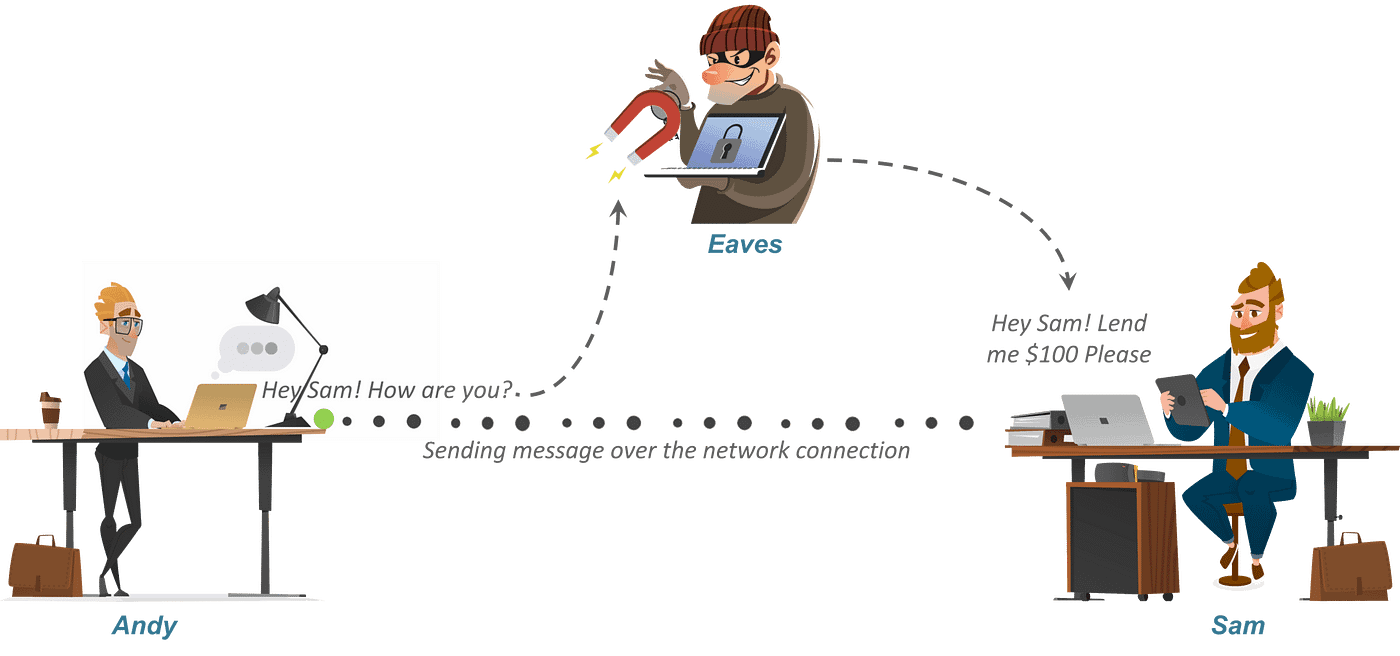
Let’s say there’s a sensible man referred to as Eaves who secretly obtained entry to your communication channel. Since this man has entry to your communication, he can do way more than simply eavesdropping, for instance, he can attempt to change the message. Now, that is only a small instance. What if Eave will get entry to your personal info? The outcome may very well be catastrophic.
So how can Andy make sure that no person within the center may entry the message despatched to Sam? That’s the place Encryption or Cryptography is available in. Let me let you know ” What’s Cryptography “.
Cryptography is the apply and examine of strategies for securing communication and knowledge within the presence of adversaries.

Alright, now that you realize ” what’s cryptography ” let’s see how cryptography can assist safe the connection between Andy and Sam.
So, to guard his message, Andy first converts his readable message to unreadable kind. Right here, he converts the message to some random numbers. After that, he makes use of a key to encrypt his message, in Cryptography, we name this ciphertext.
Andy sends this ciphertext or encrypted message over the communication channel, he received’t have to fret about someone in the course of discovering his personal messages. Suppose, Eaves right here uncover the message and he one way or the other manages to change it earlier than it reaches Sam.
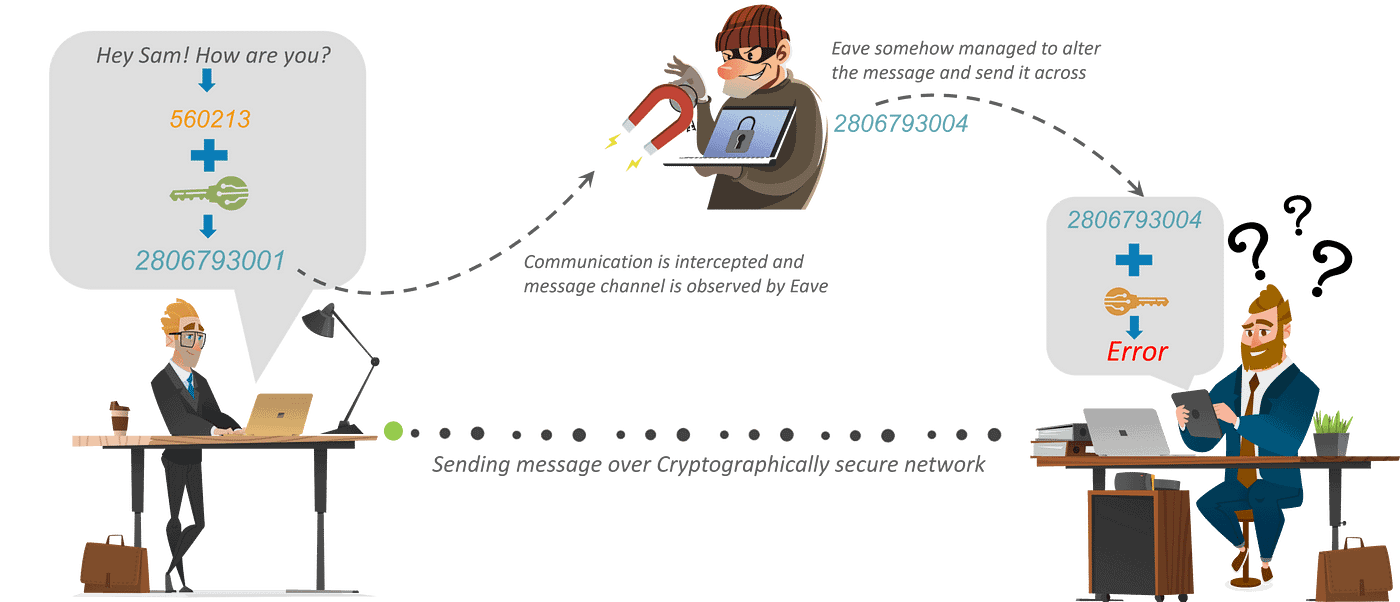
Now, Sam would wish a key to decrypt the message to get better the unique plaintext. With a purpose to convert the ciphertext into plain textual content, Sam would wish to make use of the decryption key. Utilizing the important thing he would convert the ciphertext or the numerical worth to the corresponding plain textual content.
After utilizing the important thing for decryption what is going to come out is the unique plaintext message, is an error. Now, this error is essential. It’s the means Sam is aware of that message despatched by Andy isn’t the identical because the message that he obtained. Thus, we will say that encryption is vital to speak or share info over the community.
Cryptography is broadly categorised into two classes: Symmetric key Cryptography and Uneven key Cryptography (popularly referred to as public key cryptography).

Now Symmetric key Cryptography is additional categorized as Classical Cryptography and Fashionable Cryptography.
Additional drilling down, Classical Cryptography is split into Transposition Cipher and Substitution Cipher. However, Fashionable Cryptography is split into Stream Cipher and Block Cipher.
So, let’s perceive these algorithms with examples.
Let’s begin with the Symmetric key encryption
Symmetric Key Cryptography
An encryption system wherein the sender and receiver of a message share a single, frequent key that’s used to encrypt and decrypt the message. The most well-liked symmetric–key system is the Knowledge Encryption Normal (DES).

Transposition Ciphers
In Cryptography, a transposition cipher is a technique of encryption by which the positions held by models of plaintext (that are generally characters or teams of characters) are shifted based on a daily system, in order that the ciphertext constitutes a permutation of the plaintext.
That’s, the order of the models is modified (the plaintext is reordered). Mathematically, a bijective perform is used on the characters’ positions to encrypt and an inverse perform to decrypt.
Instance:

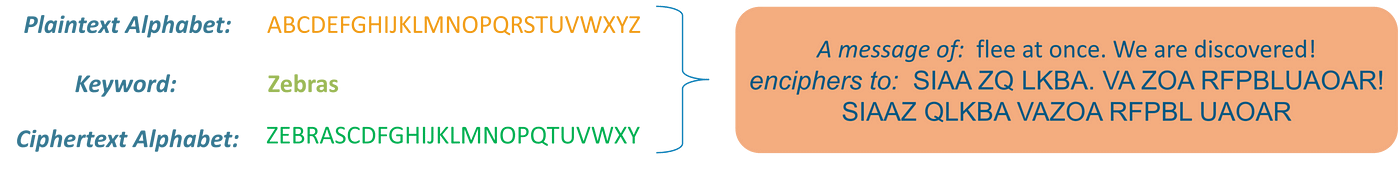
Substitution Cipher
Methodology of encryption by which models of plaintext are changed with ciphertext, based on a hard and fast system; the “models” could also be single letters (the commonest), pairs of letters, triplets of letters, mixtures of the above, and so forth.
Instance:
Contemplate this instance proven on the slide: Utilizing the system simply mentioned, the key phrase “zebras” provides us the next alphabets:
Stream Cipher
Symmetric or secret-key encryption algorithm that encrypts a single bit at a time. With a Stream Cipher, the identical plaintext bit or byte will encrypt to a special bit or byte each time it’s encrypted.

Block Cipher
An encryption technique that applies a deterministic algorithm together with a symmetric key to encrypt a block of textual content, somewhat than encrypting one bit at a time as in stream ciphers

Instance: A standard block cipher, AES, encrypts 128-bit blocks with a key of predetermined size: 128, 192, or 256 bits. Block ciphers are pseudorandom permutation (PRP) households that function on the fastened dimension block of bits. PRPs are features that can’t be differentiated from fully random permutations and thus, are thought of dependable till confirmed unreliable.
The encryption course of the place completely different keys are used for encrypting and decrypting the data. Keys are completely different however are mathematically associated, such that retrieving the plain textual content by decrypting ciphertext is possible.

RSA is essentially the most broadly used type of public key encryption,
RSA Algorithm
- RSA stands for Rivest, Shamir, and Adelman, inventors of this system
- Each private and non-private key are interchangeable
- Variable Key Measurement (512, 1024, or 2048 bits)
Right here’s how keys are generated in RSA algorithm

Conclusion
Alright, this was it for “What’s Cryptography” article. To safeguard your info and knowledge shared over the web you will need to use sturdy encryption algorithms, to keep away from any catastrophic conditions.
This brings us to the tip of our article on What’s Cryptography? I hope you discovered this text informative and added worth to your information.
